MSP Technology News Headlines for the Week of 12/01/2025
Wasabi’s new ransomware-resistant feature “Covert Copy” takes top billing this week, but our first week in December marks the beginning of a deluge of year-end reports and predictions for next year… some of which should be very interesting to MSPs, MSSPs, and IT admins alike.
Ready for a quick rundown of this week’s MSP news and partner program updates? Scroll on down!
Wasabi Launches Covert Copy — A Completely Invisible and Indestructible Copy of Data for a Higher Level of Cloud Storage Security
Wasabi introduces “Covert Copy,” a patent-pending ransomware-resistant feature that creates a hidden, immutable copy of storage data to fortify cloud storage security and resilience.
Key quote from the press release:
“Organizations are under increasing pressure, both internally and from regulators, to ensure that their data is untouchable. However, implementing strategic data protection programs is often difficult, time-consuming, and expensive. Covert Copy enables enterprises to seamlessly and affordably ensure their data is completely hidden from bad actors and ransomware attacks. For cyber attackers, you can’t attack what you can’t see.” — David Boland, vice president of cloud strategy, Wasabi Technologies
Syncro and CyberDrain Launch Snapshot — Free Microsoft Tenant Security Assessment for MSPs
New assessment delivers fast insights to help MSPs strengthen Microsoft 365 security posture, reduce risk and support sales efforts.
Key quote from the press release:
“Every MSP I talk to says the same thing — they want fast, reliable security assessments without the friction that slows down a sales conversation. We listened. That’s why we partnered with CyberDrain to build Syncro Snapshot. It’s fast, secure and ready to run right away. No onboarding, no accounts, no stored data. Just run an assessment, get a clean report and start selling with confidence.” — Rich Dean, senior director of product management, Syncro
Semperis Study Reveals that the Majority of Ransomware Attacks Continue to Occur During Holidays and Weekends

Organizations should prepare for a surge in ransomware attacks during holidays, weekends, and major corporate events, when cybersecurity staffing is its weakest.
Key findings from the report include:
- 52% of surveyed organizations across 10 countries were targeted with ransomware on holidays or weekends.
- 78% of companies cut security operations center (SOC) staffing by 50% or more during holidays and weekends, and 6% eliminate SOC staffing entirely during these periods.
- 60% of ransomware attacks occurred following a material corporate event such as an IPO, merger or acquisition, or round of layoffs; among those attacked after such an event, 54% were targeted following a merger or acquisition.
- Top reasons for reducing SOC staffing on holidays and weekends include providing work/life balance (62%), being closed for business (47%), and believing they would not be attacked (29%).
- While 90% of respondents report that their identity threat detection and response (ITDR) plans detect identity system vulnerabilities, only 45% include remediation procedures and just 63% automate identity system recovery.
ClickFix Gets Creative: Malware Buried in Images
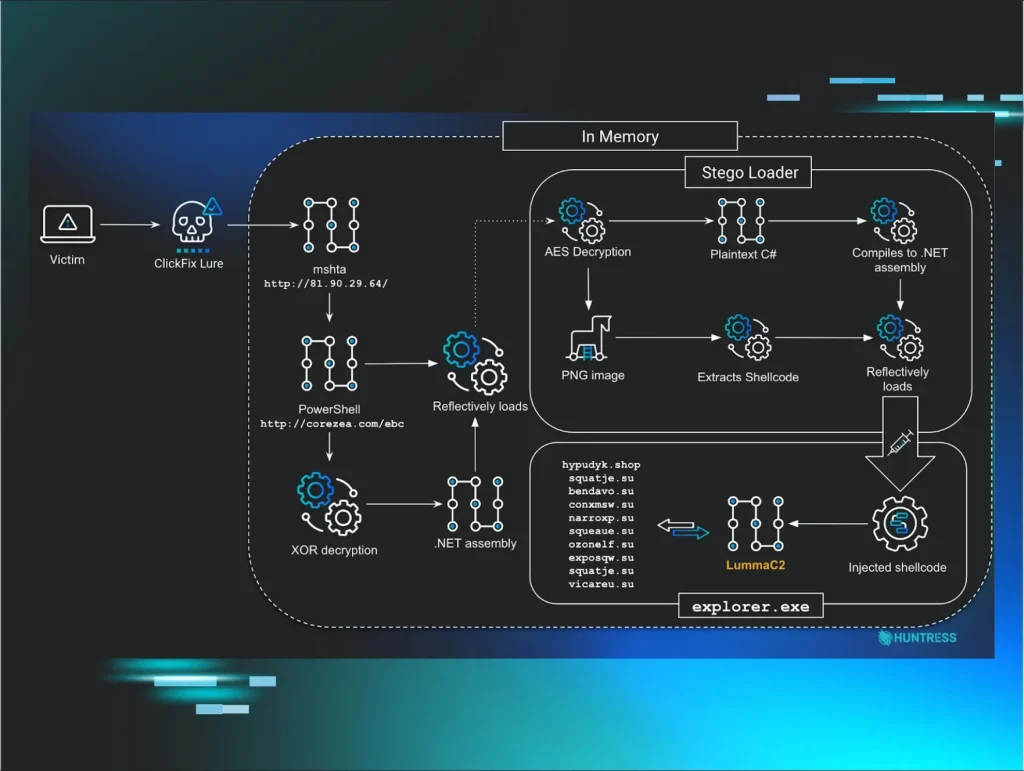
New variant of the ClickFix campaign hides infostealer malware inside image files, using fake update screens and steganography.
Key findings from the blog post include:
- The campaign delivers infostealing malware — including LummaC2 and Rhadamanthys — via a multi-stage execution chain initiated by ClickFix social-engineering lures.
- Attackers are now embedding the final malware payload within PNG image files: malicious code is encoded directly into pixel data and reconstructed and decrypted in memory.
- Two primary lure types have been observed: a faux “Human Verification” prompt, and a highly convincing fake full-screen Microsoft Windows Update screen prompting victims to run a pasted command.
- The execution chain starts when the victim runs a malicious mshta-launched JavaScript, triggering a PowerShell loader that decrypts a .NET assembly, which in turn loads a “stego loader” that extracts shellcode from images and injects it into running processes.
- Because the code is hidden in images and loaded in memory, the payload bypasses many traditional signature-based detection tools — making this a stealthy and sophisticated threat.
NeuralTrust Introduces Guardian Agents — First AI Agents Built to Protect Other Agents
NeuralTrust says its new Guardian Agents bring real-time, autonomous security for large-scale AI-agent deployments, aiming to close gaps traditional tools can’t handle.
Key quote from the press release:
“Autonomous agents have changed the threat landscape. Defending them requires security that moves just as fast. Guardian Agents give organizations a way to stay ahead of attacks, enforce policy, and deploy AI safely at scale.” — Joan Vendrell, co-founder and CEO, NeuralTrust
Lightbeam Appoints Former CrowdStrike Channel Leader Matthew Kelly to Drive Partner-First Strategy
Cybersecurity vendor Lightbeam hires veteran channel executive Matthew Kelly as Director, Channel and Alliances — signaling a major push to scale its partner ecosystem, including MSPs, MSSPs, GSIs, and technology alliances.
Key quote from the press release:
“Lightbeam is uniquely positioned at the intersection of data security, AI governance, and privacy automation. Our goal is to empower partners with the tools, training, and trust they need to build profitable, long-term relationships with customers while helping them secure sensitive data at petabyte scale. Lightbeam’s technology is disruptive, but our approach to partnership will always be collaborative.” — Matthew Kelly, director, channel and alliances, Lightbeam
AppDirect and Tackle.io to Unite to Extend Leadership in B2B Subscription Commerce with Native Hyperscaler Marketplace Integration
The combined platform will provide unprecedented access and seamless integration to distribute and manage products through marketplaces globally.
Key quote from the press release:
“Our vision is to be the number one subscription commerce platform for buying, selling, and managing technology. With the addition of Tackle, we’re delivering on that promise—empowering our providers with turnkey cloud distribution, native billing, and unified analytics for every go-to-market channel, all in one place.” — Nicolas Desmarais, chairman and CEO, AppDirect
Keepit Publishes “Data Sovereignty: Take Control of Your Data” Report

A new report from Keepit highlights how data sovereignty conflicts pose serious risks to backup, recovery, and cyber-resilience strategies for organizations operating in the cloud.
Key findings from the report include:
- The report is hands-on: includes national snapshots, regulatory obligations and architectural risks.
- It explains why organizations are revisiting sovereign-cloud, vendor-independent backup, and hybrid recovery models.
- It provides a blueprint for building provable, regulator-ready independence between production and recovery paths
- It aligns with key important trends: resilience, cloud outages, DR architecture, continuity planning, sovereign cloud, backup gaps, and concentration risk
BlackFog Expands ADX Platform with Launch of ADX Vision to Combat Shadow AI Threats

New solution provides enterprises with visibility and control as research reveals 49% of employees use unsanctioned AI tools at work.
Key quote from the press release:
“Preventing data exfiltration has been at the core of our mission from day one, and we’ve consistently adapted our technology to stay ahead of emerging threats. ADX Vision is the next step in that journey, offering unmatched visibility into shadow AI activity so organizations can protect their data with confidence.” — Dr Darren Williams, CEO and Founder, BlackFog
SOC Threat Radar — December 2025
Barracuda Managed XDR highlights a surge in malicious actors exploiting remote-access tools, credential theft, and suspicious login activity to compromise enterprise environments.
Key findings from the report include:
- A rise in the suspicious use of ScreenConnect. This includes attackers attempting to connect endpoints to targets’ ScreenConnect deployments, and attackers deploying ScreenConnect themselves to control hosts remotely.
- An increase in Microsoft 365 login attempts from countries where the targets don’t operate. This presents a clear red flag that attackers are trying to access accounts using stolen usernames and passwords.
- How attackers are stealing or buying usernames and passwords (credentials) and using them to break into systems. These attacks often resemble normal activity because the hackers use genuine credentials. Once inside, the attackers may initiate ransomware attacks or steal sensitive data.
More from Barracuda
➡️ Threat Spotlight: Introducing GhostFrame, a new super stealthy phishing kit
VISO Wins Nanitor Partner of the Year 2025 for Excellence in CTEM Delivery Across UK and Ireland
Nanitor names VISO as its inaugural Partner of the Year, recognizing standout growth, collaboration, and customer impact in delivering CTEM across the region.
Key quote from the ChannelPro press release coverage:
“VISO’s enthusiasm, customer focus, and rapid execution stood out from day one. Their ability to translate CTEM into real operational value for clients has made them a model partner for our ecosystem. As our partner program expands across Europe, the UK, the Middle East, and North America, VISO represents the type of forward-thinking cybersecurity provider driving this next phase of growth.” — Heimir Fannar Gunnlaugsson, CEO, Nanitor
Flashpoint’s Top 5 Predictions for the 2026 Threat Landscape
Forward-looking threat insights from Flashpoint highlight how 2026 may bring a dramatic shift in cyber- and physical-risk dynamics — driven by AI, identity exploitation, instability in vulnerability systems, and threat convergence.
Key findings from the report include:
- AI-driven threats escalate: Attackers begin leveraging more autonomous and integrated AI systems, not just model-based exploits.
- Identity becomes the new battleground: Infostealers to fuel most intrusions by capturing credentials, tokens, and cloud access.
- Vulnerability intelligence shifts: Instability in public vulnerability databases pushes organizations toward redundant, intelligence-driven tracking.
- Cyber-physical targeting grows: Threat actors increasingly target executives and individuals as digital and physical risks fully converge.
- Supply-chain risk intensifies: Identity-based compromise and third-party access become prime vectors for extortion and infiltration.
Kevin Lancaster Joins usecure’s Board to Accelerate North American Channel Growth
usecure is excited to announce that Kevin Lancaster has joined as a Non-Executive Director, bringing with him decades of channel leadership, cybersecurity innovation, and a proven track record of scaling partner-first businesses across the MSP ecosystem.
Key quote from the blog post:
“Kevin is an outstanding addition to usecure’s board. He brings hands-on channel leadership, deep knowledge of security awareness and human risk management, and a track record of scaling channel-first product and community businesses. Kevin will be instrumental in helping us accelerate the growth we are already seeing in the channel and expand our footprint in North America.” — Charles Preston, founder and CEO, usecure
Cybersecurity Predictions for 2026: 5 Key Risks
NordVPN experts outline five cybersecurity threats expected to escalate in 2026, highlighting how risks once associated with large enterprises are increasingly targeting everyday users.
Key findings from the report include:
- The internet’s growing dependence on a few dominant platforms — such as AWS, Cloudflare, Google Workspace, and Microsoft Office — is creating a fragile digital monoculture where a single outage, breach, or misconfiguration can disrupt millions of users. Hackers are exploiting this over-reliance to maximize impact.
- Misinformation about online security habits is spreading rapidly across social media. False AI-generated content, human error, and coordinated criminal influence campaigns are normalizing unsafe behaviors — including password reuse and disabling security protections — making users more vulnerable.
- Malicious AI tools like Evil-GPT and WormGPT are enabling attackers to execute phishing, network breaches, and other cyberattacks with unprecedented ease and scale. AI is empowering both novice and experienced cybercriminals to launch increasingly sophisticated campaigns.
- Cybercriminals are exploiting data shared with trusted AI tools, including generative AI chatbots. Despite warnings, users continue to input sensitive information, providing attackers with valuable personal and business data.
- Organized threat groups are weaponizing influence tactics, hiring or creating fake “influencers” to promote weak security products and poor cybersecurity habits — intentionally expanding the pool of vulnerable potential victims.
Russian-Backed RomCom Uses SocGholish to Deliver Mythic Agent to U.S. Companies Supporting Ukraine
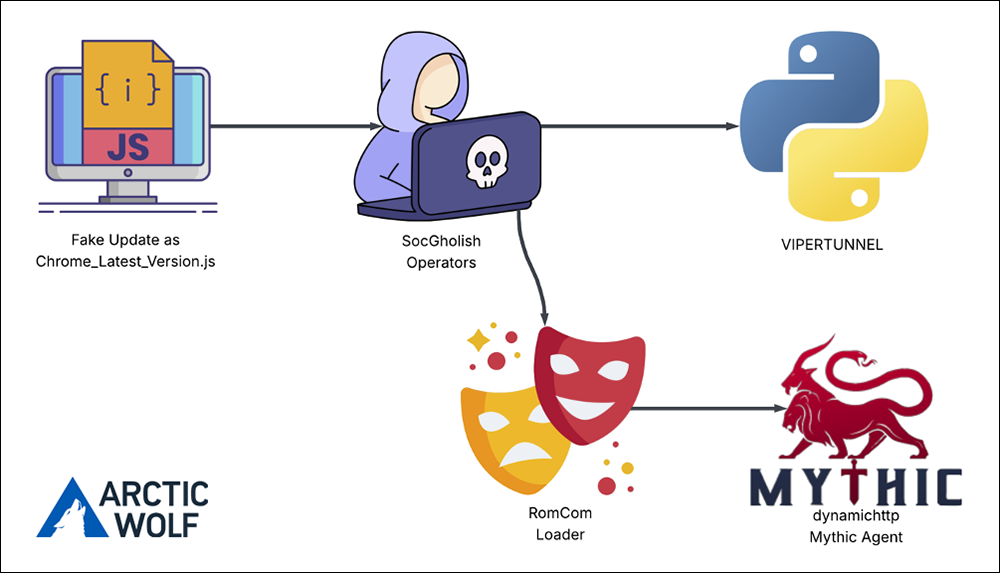
Arctic Wolf Labs recently identified the first-known instance of the RomCom threat group using SocGholish fake-update lures to deliver Mythic Agent to a U.S.-based civil-engineering firm with ties to Ukraine.
Key findings from the report include:
- In September 2025, Arctic Wolf Labs uncovered the first confirmed instance of RomCom malware being distributed via SocGholish, marking a significant escalation in both actors’ tactics.
- In a recent incident targeting a U.S. engineering firm with ties to Ukraine, TA569’s SocGholish framework delivered RomCom’s Mythic Agent loader within minutes of initial compromise.
- Evidence strongly links this activity to Russia’s GRU Unit 29155, underscoring its continued focus on disrupting pro-Ukraine entities worldwide.
Hack The Box Launches the World’s First AI Cyber Range to Benchmark AI Agents and Accelerate Human-AI Teaming Across Offensive and Defensive Cyber Operations
HTB unveils HTB AI Range — a controlled cyber-range designed to test and benchmark autonomous AI security agents alongside human operators under live-fire conditions.
Key quote from the press release:
“AI is now part of the cyber battle and overall ecosystem, and we’re building the arena where it can safely be tested and used to defend responsibly. For over two years, we’ve been advancing AI-driven learning paths, labs, and research where machines and humans compete, collaborate, and co-evolve. With HTB AI Range, we’re not reacting to AI’s rise in cyber; we’re defining how defense evolves alongside it. This is how cybersecurity advances: not through fear, but through mastery.” — Haris Pylarinos, CEO and founder, Hack The Box
SentinelOne Unveils New Innovations and Integrations with AWS to Accelerate Customers’ AI Initiatives at AWS re:Invent 2025
SentinelOne announces a suite of new integrations and offerings designed to give AWS customers unified visibility, AI-powered security, and simplified deployment across cloud workloads, endpoints, identity, and GenAI applications.
Key quote from the press release:
“Security data is the fuel that powers AI-driven, autonomous security. SentinelOne in collaboration with AWS has long believed that open platforms, open data standards like OCSF, and intelligent, unified data lakes are key to protecting customers’ ever growing attack surface — from endpoints to the cloud to AI.” — Ely Kahn, chief product officer, SentinelOne
Zenity Expands AI Security with Incident Intelligence, Agentic Browser Support, and New Open-Source Tool
Zenity extends its agent-centric security platform to cover new attack surfaces — including browser-based AI agents — and introduces enhanced incident intelligence and open-source tooling to help enterprises govern AI safely.
Key quote from the press release:
“With this release we are giving security teams something they have never had before, real visibility into intent. Our new Correlation Agent does not just detect signals, it interprets them. It understands what an agent is trying to do, by connecting every signal, data point and insight that the Zenity platform collects and generates throughout the agent lifecycle into a single coherent story.” — Ben Kliger, Co-Founder and CEO, Zenity
As ChannelPro’s online director and tech editor for over a decade, Matt Whitlock has spent years blending sharp tech insight with digital know-how. He brings more than 25 years’ experience working in the technology industry to his reviews, analysis, and general musings about all things gadget and gear.
Images: Semperis, Huntress, Keepit, BlackFog, usecure, Arctic Wolf